QUESTION 1.For each of the following applications, determine whether TCP or UDP is used as the transport layer protocol and explain the reason(s) for your choice [5 x 2 = 10]
a)File Transfer
b)Watching a real time streamed video
c)Web browsing
d)A Voice over IP (VoIP) telephone conversation
Solution
a)File transfer :This should be TCP The reason is that you want a file to be transmitted in its entirety without any errors, therefore the error detection and correction properties of TCP are needed.
b)Watching a real time streamed video :This should be UDP. The reason is that when watching a movie, delay is critical and therefore there simply isn't any time to seek the retransmission of any errors. The simplicity of UDP is therefore required.
c)Web browsing :This should be TCP The reason is that web pages need to be delivered without error so that all content is properly formatted and presented. Therefore the error detection and correction properties of TCP are needed.
d)A Voice over IP (VoIP) telephone conversation :This should be UDP. The reason is that a telephone conversation has strict timing requirements for the transfer of data and seeking the retransmission of any errors would introduce too much delay. Therefore the simplicity of UDP is needed.
QUESTION 2(i) Consider two hosts, A and B, connected by a single link of rate R bps. Suppose that the two hosts are separated by m meters, and suppose the propagation speed along the link is s meters/sec. Host A is to send a packet of size L bits to Host B. [5 x 1 = 5]
a. Express the propagation delay, dprop, in terms of m and s.
b. Ignoring processing and queuing delays, obtain an expression for the end-to-end delay.
c. Suppose Host Abegins to transmit the packet at time t = 0. At time t = dtrans, where
is the last bit of the packet?
d. Suppose dprop is greater than dtrans. At time t = dtrans, where is the first bit of the
packet?
e. Suppose dprop is less than dtrans. At time t = dtrans, where is the first bit of the packet?
QUESTION 2(ii)This elementary problem begins to explore propagation delay and transmission delay, two central concepts in data networking. Consider two hosts, A and B, connected by a single link of rate R bps. Suppose that the two hosts are separated by m meters, and suppose the propagation speed along the link is s meters/sec. Host A is to send a packet of size L bits to Host B.
a. Express the propagation delay, dprop, in terms of m and s.
b. Determine the transmission time of the packet, dtrans, in terms of L and R.
c. Ignoring processing and queuing delays, obtain an expression for the end-toend delay.
d. Suppose Host A begins to transmit the packet at time t=0. At time t=dtrans, where is the last bit of the packet?
e. Suppose dprop is greater than dtrans. At time t=dtrans, where is the first bit of the packet?
f. Suppose dprop is less than dtrans. At time t=dtrans, where is the first bit of the packet?
g. Suppose s=2*109, L=1024 bits, and R=256 kbps. Find the distance m so that dprop equals dtrans.
Solution:
QUESTION 2(iii)What is crosstalk? How is it minimized in case of twisted-pair of wire?[3M]
Solution:
QUESTION 2(iv) The following encoding is used in data link protocol [2M]
A: 01000111; B: 11100011; FLAG: 01111110; ESC: 11100000 show the bit sequence transmitted for the four-character frame: A B ESC FLAG using Staring and ending flag bytes, with bit stuffing
Solution:
Flag bytes with byte stuffing
Starting and ending flag bytes, with bit stuffing
QUESTION 3.i) Hosts A and B are communicating over a TCP connection, and Host B has already received from A all bytes up through byte 126. Suppose Host A then sends two segments to Host B back-to-back. The first and second segments contain 80 and 40 bytes of data, respectively. In the first segment, the sequence number is 127, the source port number is 302, and the destination port number is 80. Host B sends an acknowledgment whenever it receives a segment from Host A. [4 x 2=8]
a)In the second segment sent from Host A to B, what are the sequence number, source port number, and destination port number?
Solution:
The sequence number is 127 + 80 = 207, the source port number is 302, and the destination port number is 80.
b) If the first segment arrives before the second segment, in the acknowledgment of the first arriving segment, what is the acknowledgment number, the source port number, and the destination port number?
Solution:
The acknowledgement number is 207, source port number is 80 and the destination port number is 302.
c) If the second segment arrives before the first segment, in the ACK of the first arriving segment, what is the ACK number?
Solution:
The acknowledgement number is 127, indicating that it is still waiting for bytes 127 and onwards.
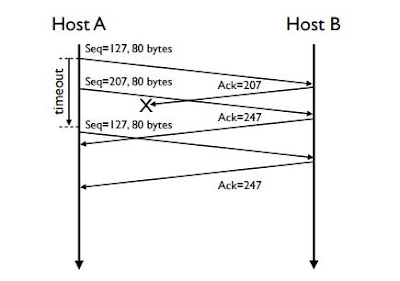
d)Suppose the two segments sent by A arrive in order at B. The first acknowledgment is lost and the second acknowledgment arrives after the first timeout interval. Draw a timing diagram, showing these segments and all other segments and acknowledgments sent. (Assume there is no additional packet loss.) For each segment in your figure, provide the sequence number and the number of bytes of data; for each acknowledgment that you add, provide the acknowledgment number.
Solution:
QUESTION 3.ii) Amongst OSPF & RIP protocols, which would you choose for a very large network and why ?[2 M]
QUESTION 4.Imagine you are a consultant being asked to provide advice on the design of a new network. A company is moving onto a new industrial estate and will be taking over the use of three buildings (A, B and C). The buildings are only 40 metres apart and the company is aware that a network of underground cable ducts exists linking the three buildings. All the buildings only have one floor and each measure about 50 metres by 20 metres. The company will be operating several web servers which are intended to be accessible from external locations by customers.Building A contains the company's main computer room which holds the web servers and also contains several database and file servers used by the company's staff. The building also contains the offices of some development staff who have very high performance desktop computers. Their computers interactively exchange large amounts of data with some of the servers.Building B contains the office of the clerical staff. They have relatively low performance desktop computers and their desks are in fixed locations. The workers only exchange a small amount of data with the servers.
Building C contains the staff cafe and a lounge area. There are also areas used to welcome customers. Much of the building is open plan and the furniture is regularly moved around. [10 M]
a) What type of networking should be installed in building A and what equipmentor other facilities would you need? [2]
b) What type of networking should be installed in building B and what equipment or other facilities would you need?[2]
c) What type of networking should be installed in building C and what equipment or other facilities would you need? How will you try to provide internet access for visiting customers without compromising the safety of the company's own computers? [3]
d) What type of networking and equipment should be used to link together the three buildings and how will overall Internet access be provided for the company?[3]
QUESTION 5.(i)For the network 192.48.24.0/21, answer the following questions: [6M]
(a) How many IP addresses can be allocated?
(b) What is the last possible host IP address ?
(c) What is the netmask?
Solution:
(a)232−21 = 211 = 2048.
(b)(31 + 1 − 24) × 256 = 2048 ⇒ 192.48.31.255.
(c)The host ranges from 192.48.24.0 to 192.48.31.255. The first, second, and forth part of the netmask are 255, 255, and 0, respectively. The third part of the netmask 256 − 224−21 = 248. Hence, the netmask is 255.255.248.0.
QUESTION 5.(ii) There are 4 parties that wish to communicate to each other (two at a time) confidentially. How many keys are required if they decide to use
1).Symmetric Key encryption
2). Asymmetric Key Encryption
Please note that communication between A and B should not be visible to C and D and so on and also explain different types of firewalls [4M]
XXXXXXX
a)File Transfer
b)Watching a real time streamed video
c)Web browsing
d)A Voice over IP (VoIP) telephone conversation
Solution
a)File transfer :This should be TCP The reason is that you want a file to be transmitted in its entirety without any errors, therefore the error detection and correction properties of TCP are needed.
b)Watching a real time streamed video :This should be UDP. The reason is that when watching a movie, delay is critical and therefore there simply isn't any time to seek the retransmission of any errors. The simplicity of UDP is therefore required.
c)Web browsing :This should be TCP The reason is that web pages need to be delivered without error so that all content is properly formatted and presented. Therefore the error detection and correction properties of TCP are needed.
d)A Voice over IP (VoIP) telephone conversation :This should be UDP. The reason is that a telephone conversation has strict timing requirements for the transfer of data and seeking the retransmission of any errors would introduce too much delay. Therefore the simplicity of UDP is needed.
QUESTION 2(i) Consider two hosts, A and B, connected by a single link of rate R bps. Suppose that the two hosts are separated by m meters, and suppose the propagation speed along the link is s meters/sec. Host A is to send a packet of size L bits to Host B. [5 x 1 = 5]
a. Express the propagation delay, dprop, in terms of m and s.
b. Ignoring processing and queuing delays, obtain an expression for the end-to-end delay.
c. Suppose Host Abegins to transmit the packet at time t = 0. At time t = dtrans, where
is the last bit of the packet?
d. Suppose dprop is greater than dtrans. At time t = dtrans, where is the first bit of the
packet?
e. Suppose dprop is less than dtrans. At time t = dtrans, where is the first bit of the packet?
QUESTION 2(ii)This elementary problem begins to explore propagation delay and transmission delay, two central concepts in data networking. Consider two hosts, A and B, connected by a single link of rate R bps. Suppose that the two hosts are separated by m meters, and suppose the propagation speed along the link is s meters/sec. Host A is to send a packet of size L bits to Host B.
a. Express the propagation delay, dprop, in terms of m and s.
b. Determine the transmission time of the packet, dtrans, in terms of L and R.
c. Ignoring processing and queuing delays, obtain an expression for the end-toend delay.
d. Suppose Host A begins to transmit the packet at time t=0. At time t=dtrans, where is the last bit of the packet?
e. Suppose dprop is greater than dtrans. At time t=dtrans, where is the first bit of the packet?
f. Suppose dprop is less than dtrans. At time t=dtrans, where is the first bit of the packet?
g. Suppose s=2*109, L=1024 bits, and R=256 kbps. Find the distance m so that dprop equals dtrans.
Solution:
QUESTION 2(iii)What is crosstalk? How is it minimized in case of twisted-pair of wire?[3M]
Solution:
QUESTION 2(iv) The following encoding is used in data link protocol [2M]
A: 01000111; B: 11100011; FLAG: 01111110; ESC: 11100000 show the bit sequence transmitted for the four-character frame: A B ESC FLAG using Staring and ending flag bytes, with bit stuffing
Solution:
Flag bytes with byte stuffing
Starting and ending flag bytes, with bit stuffing
QUESTION 3.i) Hosts A and B are communicating over a TCP connection, and Host B has already received from A all bytes up through byte 126. Suppose Host A then sends two segments to Host B back-to-back. The first and second segments contain 80 and 40 bytes of data, respectively. In the first segment, the sequence number is 127, the source port number is 302, and the destination port number is 80. Host B sends an acknowledgment whenever it receives a segment from Host A. [4 x 2=8]
a)In the second segment sent from Host A to B, what are the sequence number, source port number, and destination port number?
Solution:
The sequence number is 127 + 80 = 207, the source port number is 302, and the destination port number is 80.
b) If the first segment arrives before the second segment, in the acknowledgment of the first arriving segment, what is the acknowledgment number, the source port number, and the destination port number?
Solution:
The acknowledgement number is 207, source port number is 80 and the destination port number is 302.
c) If the second segment arrives before the first segment, in the ACK of the first arriving segment, what is the ACK number?
Solution:
The acknowledgement number is 127, indicating that it is still waiting for bytes 127 and onwards.
d)Suppose the two segments sent by A arrive in order at B. The first acknowledgment is lost and the second acknowledgment arrives after the first timeout interval. Draw a timing diagram, showing these segments and all other segments and acknowledgments sent. (Assume there is no additional packet loss.) For each segment in your figure, provide the sequence number and the number of bytes of data; for each acknowledgment that you add, provide the acknowledgment number.
Solution:
QUESTION 3.ii) Amongst OSPF & RIP protocols, which would you choose for a very large network and why ?[2 M]
QUESTION 4.Imagine you are a consultant being asked to provide advice on the design of a new network. A company is moving onto a new industrial estate and will be taking over the use of three buildings (A, B and C). The buildings are only 40 metres apart and the company is aware that a network of underground cable ducts exists linking the three buildings. All the buildings only have one floor and each measure about 50 metres by 20 metres. The company will be operating several web servers which are intended to be accessible from external locations by customers.Building A contains the company's main computer room which holds the web servers and also contains several database and file servers used by the company's staff. The building also contains the offices of some development staff who have very high performance desktop computers. Their computers interactively exchange large amounts of data with some of the servers.Building B contains the office of the clerical staff. They have relatively low performance desktop computers and their desks are in fixed locations. The workers only exchange a small amount of data with the servers.
Building C contains the staff cafe and a lounge area. There are also areas used to welcome customers. Much of the building is open plan and the furniture is regularly moved around. [10 M]
a) What type of networking should be installed in building A and what equipmentor other facilities would you need? [2]
b) What type of networking should be installed in building B and what equipment or other facilities would you need?[2]
c) What type of networking should be installed in building C and what equipment or other facilities would you need? How will you try to provide internet access for visiting customers without compromising the safety of the company's own computers? [3]
d) What type of networking and equipment should be used to link together the three buildings and how will overall Internet access be provided for the company?[3]
QUESTION 5.(i)For the network 192.48.24.0/21, answer the following questions: [6M]
(a) How many IP addresses can be allocated?
(b) What is the last possible host IP address ?
(c) What is the netmask?
Solution:
(a)232−21 = 211 = 2048.
(b)(31 + 1 − 24) × 256 = 2048 ⇒ 192.48.31.255.
(c)The host ranges from 192.48.24.0 to 192.48.31.255. The first, second, and forth part of the netmask are 255, 255, and 0, respectively. The third part of the netmask 256 − 224−21 = 248. Hence, the netmask is 255.255.248.0.
QUESTION 5.(ii) There are 4 parties that wish to communicate to each other (two at a time) confidentially. How many keys are required if they decide to use
1).Symmetric Key encryption
2). Asymmetric Key Encryption
Please note that communication between A and B should not be visible to C and D and so on and also explain different types of firewalls [4M]
XXXXXXX








No comments:
Post a Comment